Abstract
This blog post outlines three vulnerabilities discovered in Feripro. These are:
- An Incorrect Access Control vulnerability in the user management system (CVE-2024-41517), which allows viewing of administrative users and their privileges.
- An Incorrect Access Control vulnerability in the statistics endpoint (CVE-2024-41518), which permits the export of statistics without the need to log in.
- A Stored Cross-Site Scripting vulnerability (CVE-2024-41519) that enables malicious code to be injected and stored in the application and executed by the user.
Thanks to the manufacturer’s extremely rapid response, a fix was available on the same day the vulnerabilities were reported and was deployed to all customer systems immediately.
What is Feripro?
Feripro is a software solution designed to simplify the management of holiday programs. It automates tasks from registration to payment, reducing administrative stress and saving time. The platform offers features like customizable registration forms, multiple payment options, email notifications, and export functions for program booklets [1]. Feripro is used by over 400 municipalities and cities, handling sensitive data with a strong focus on data protection. It provides a user-friendly interface, continuous support, and is constantly improved based on user feedback [2].
Vulnerabilities in Feripro
This section details three significant vulnerabilities found in Feripro. The first, an Incorrect Access Control issue in the user management interface (CVE-2024-41517), allows unauthorized viewing of administrative users and their privileges. The second, another Incorrect Access Control problem in the statistics endpoint (CVE-2024-41518), permits the download of statistical data without logging in. The third vulnerability is a Stored Cross-Site Scripting (XSS) flaw (CVE-2024-41519) that enables JavaScript injection via the school input field during registration, leading to malicious code execution in the registration overview. Each vulnerability poses a risk to data security and system integrity.
Incorrect Access Control in User Management Interface (CVE-2024-41517)
The Incorrect Access Control vulnerability in Feripro allows unauthorized users to view all registered (administrative) users and their privileges without needing to log in. This security flaw exposes sensitive user information. Accessible via the path /admin/benutzer/institution/rechteverwaltung/uebersicht and identified as CVE-2024-41517, this issue compromises the confidentiality of the user management system, posing a risk to the security of the affected platforms.
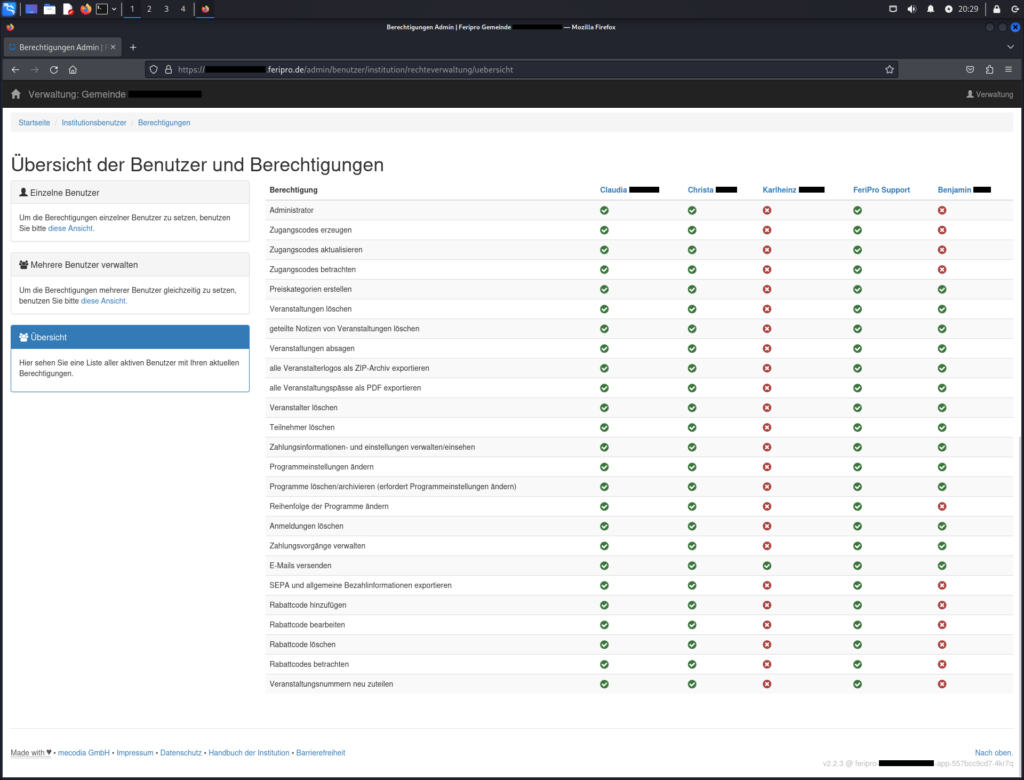
Incorrect Access Control in Statistics Endpoint (CVE-2024-41518)
The Incorrect Access Control vulnerability in Feripro’s statistics endpoint allows attackers to download statistical data as an Excel file (XLSX) without needing to log in. Accessible via the path /admin/programm/<program_id>/export/statistics and identified as CVE-2024-41518, this flaw exposes statistical data to unauthorized users, posing a risk to data confidentiality.
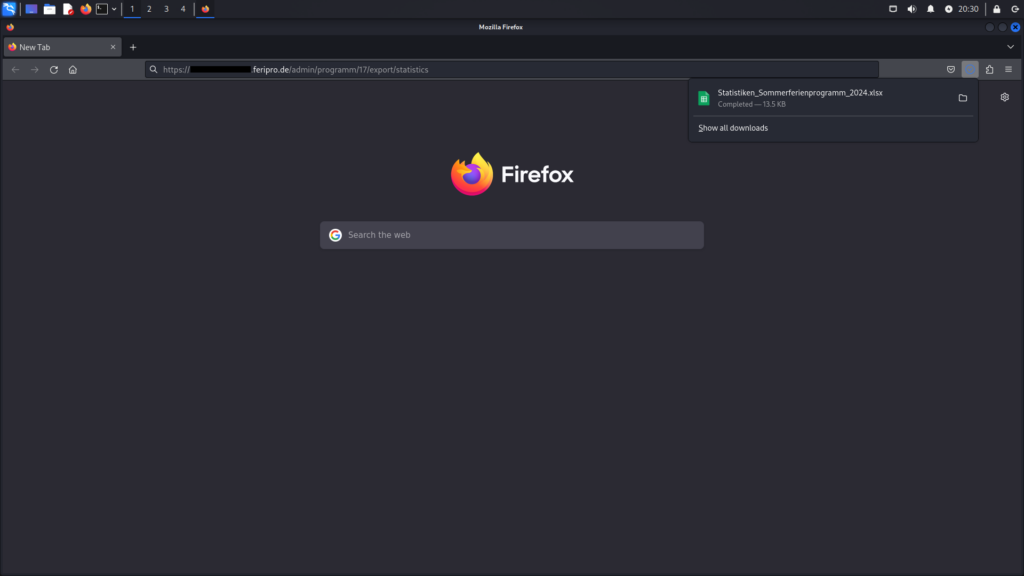
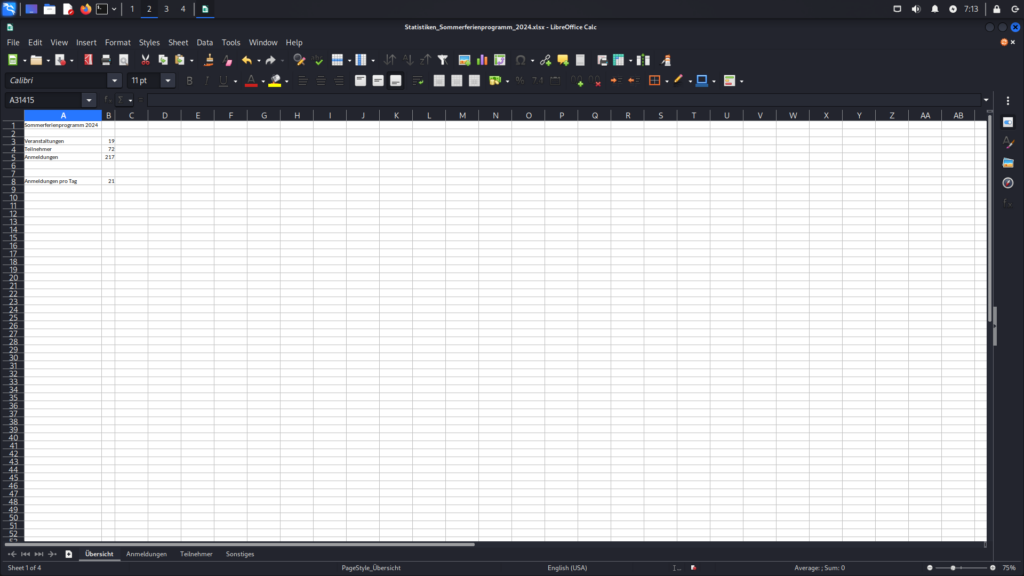
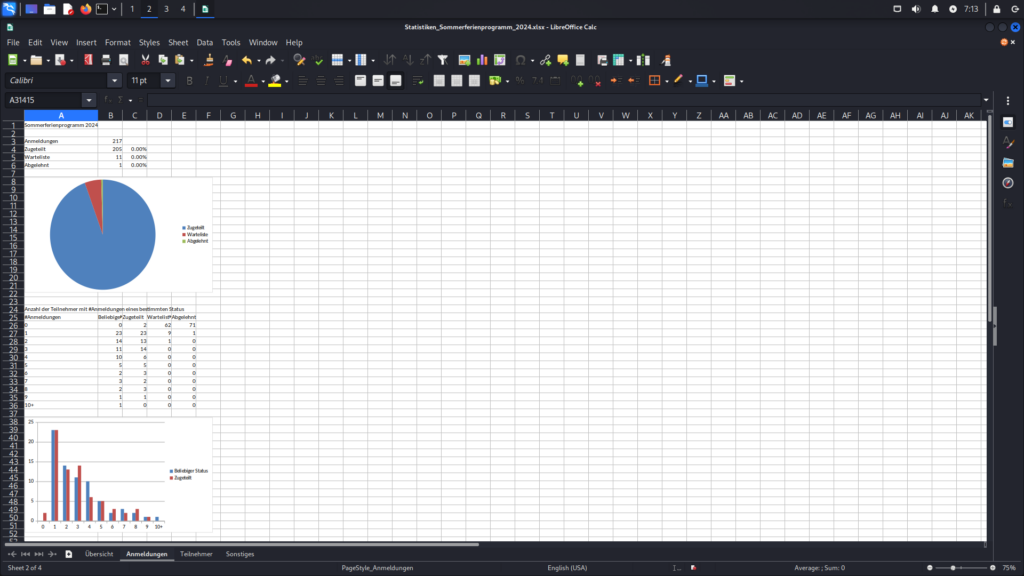
The following images display the contents of the Excel file downloaded exploiting the Incorrect Access Control vulnerability. They show detailed statistics, including the number of participants and registrations, along with information about the age and gender of the participants.
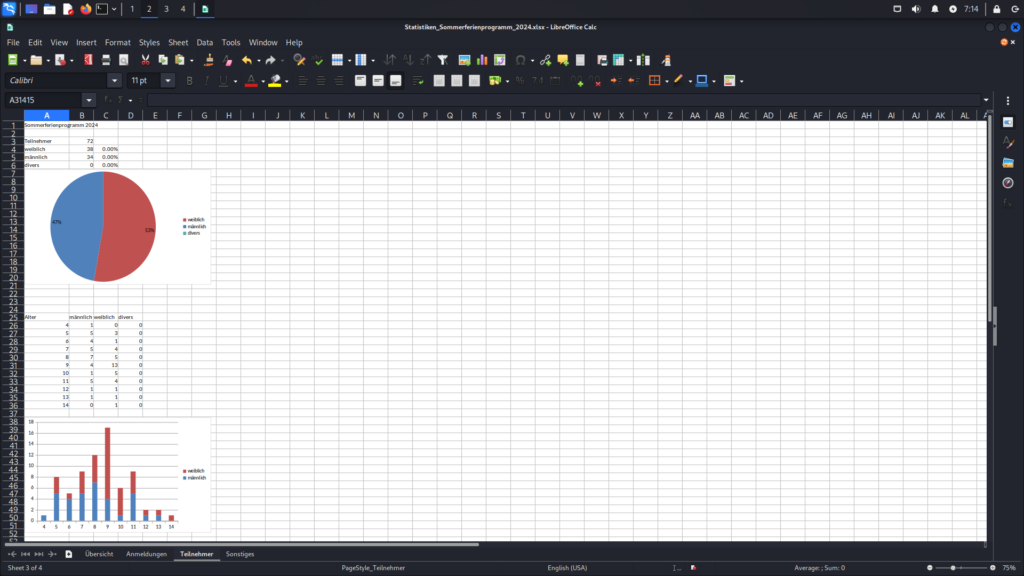
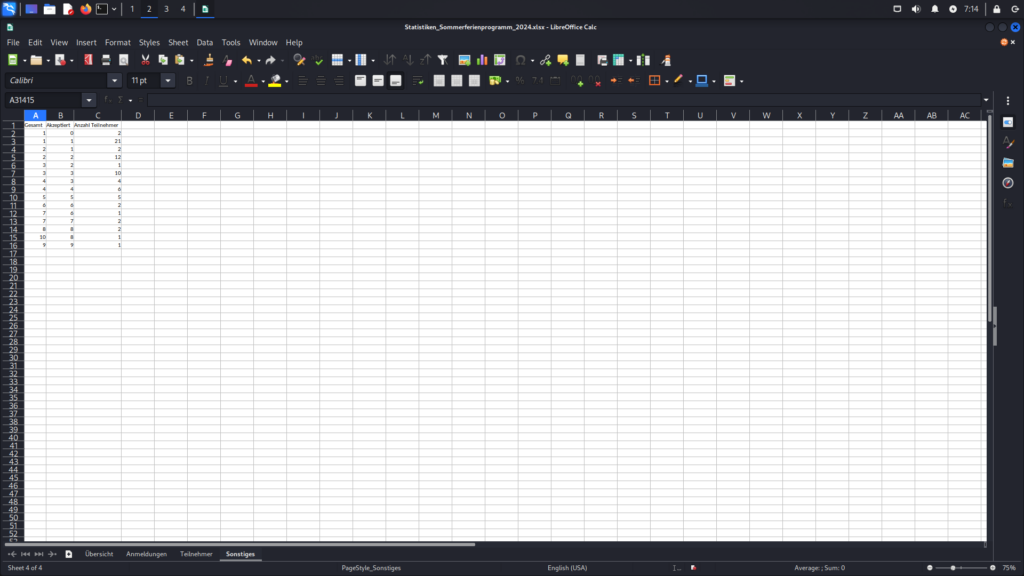
Stored XSS in Registration Overview (CVE-2024-41519)
The Stored Cross-Site Scripting (XSS) vulnerability in Feripro allows attackers to inject JavaScript via the school input field during registration. This malicious code is executed when viewing the registration overview of events. Identified as CVE-2024-41519, this flaw enables the execution of arbitrary scripts in the user’s browser, potentially leading to data theft, or other malicious activities.
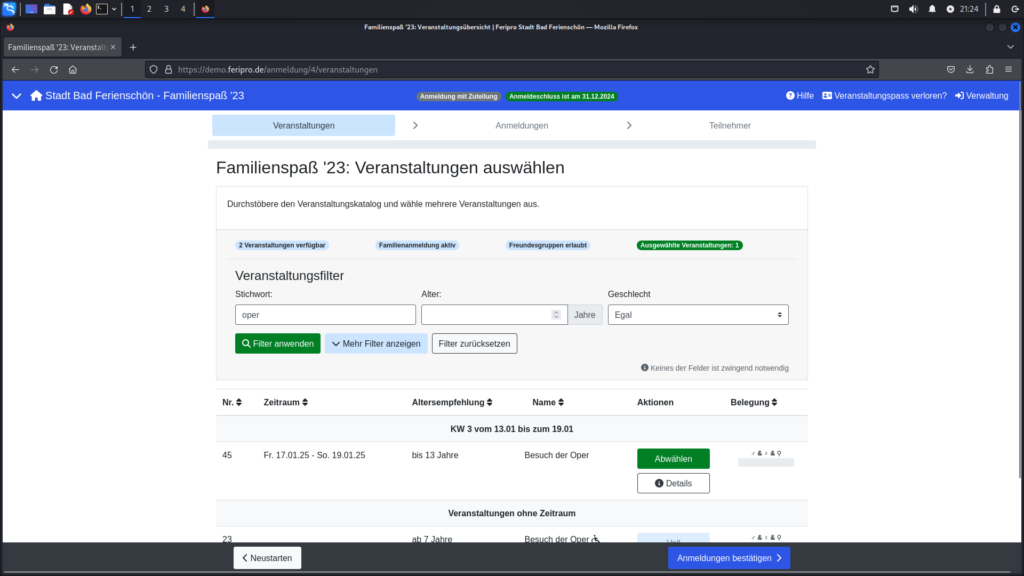
The following images demonstrate the exploitation process of the stored XSS vulnerability. The first image shows how to select an event for registration, preparing for the injection of malicious JavaScript code in subsequent steps.
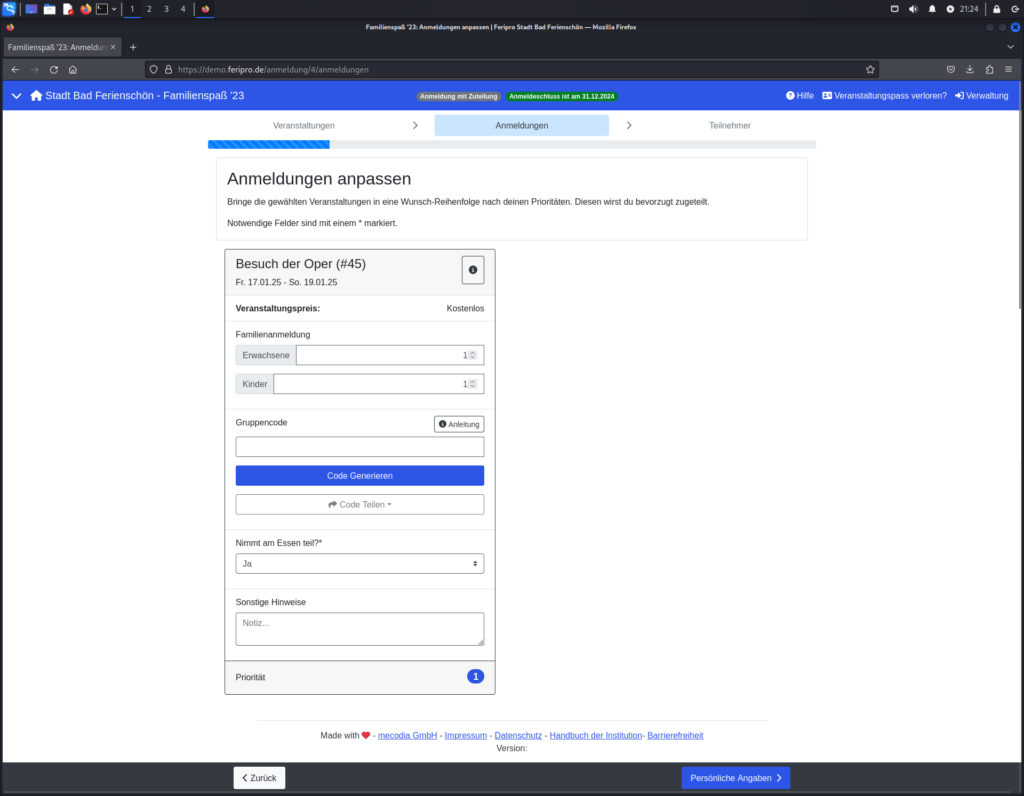
The following image continue to demonstrate the exploitation process. The next step involves entering basic information such as the number of adults and children participating in the event.
The next image shows the entry of personal information, including name, gender, and school. The school input field is vulnerable to stored XSS, allowing the injection of malicious JavaScript code.
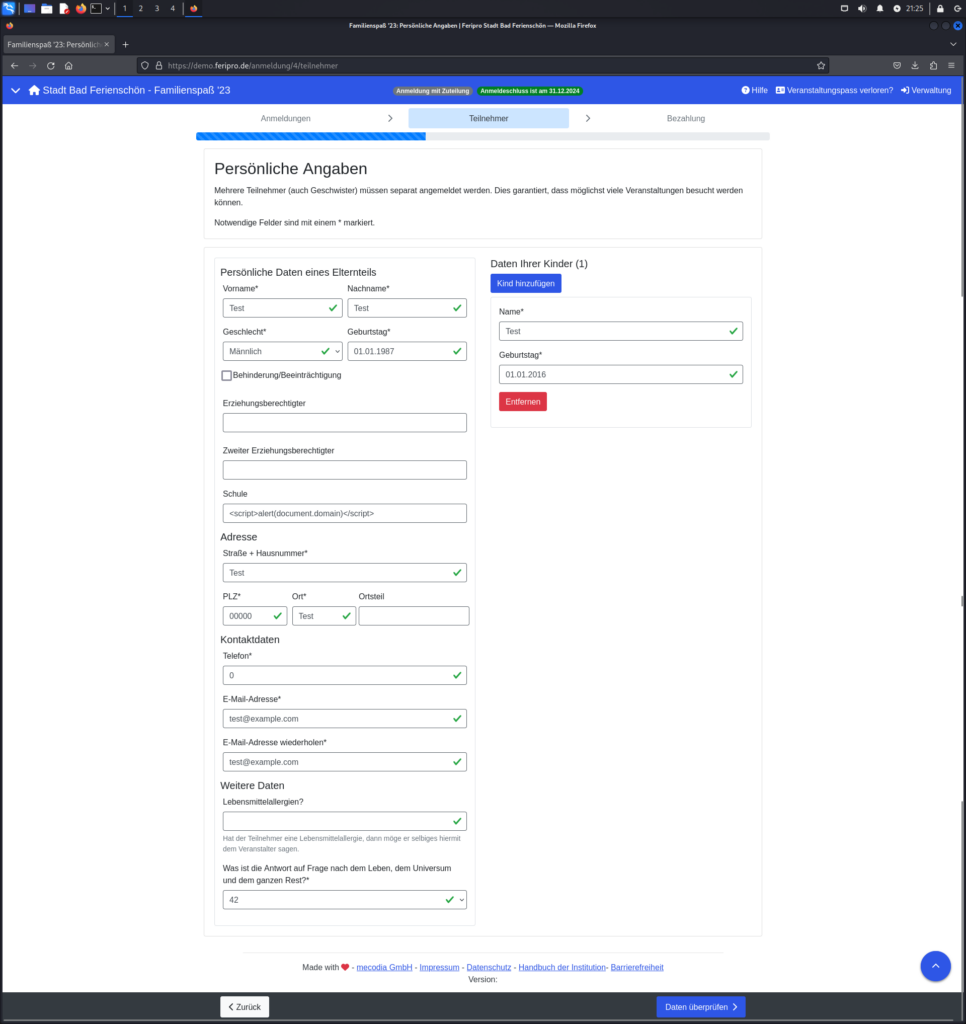
The following two images simply show the completion of the registration process and are included only for the sake of completeness.
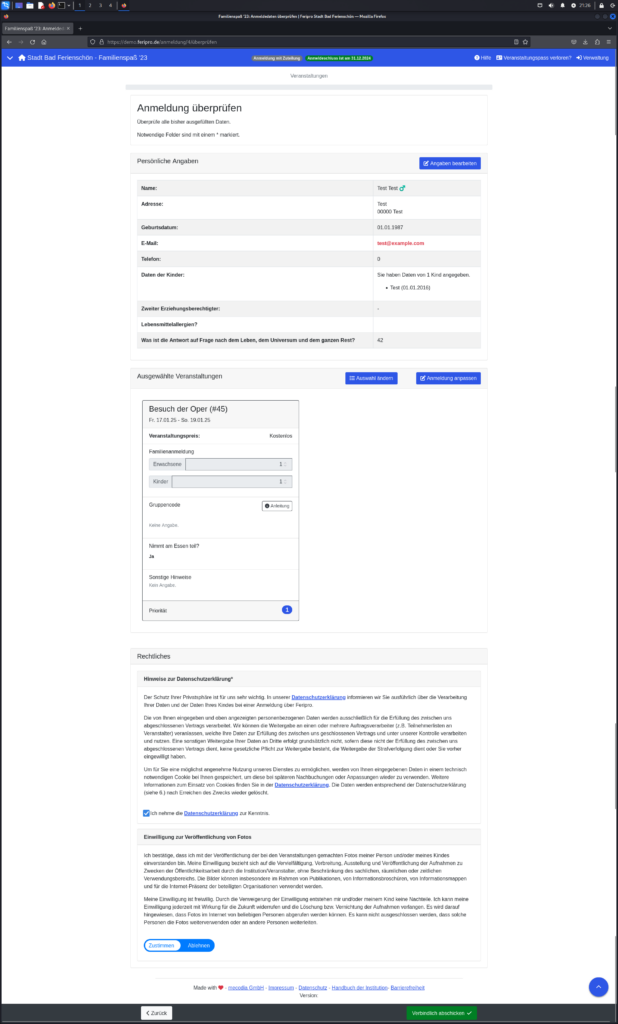
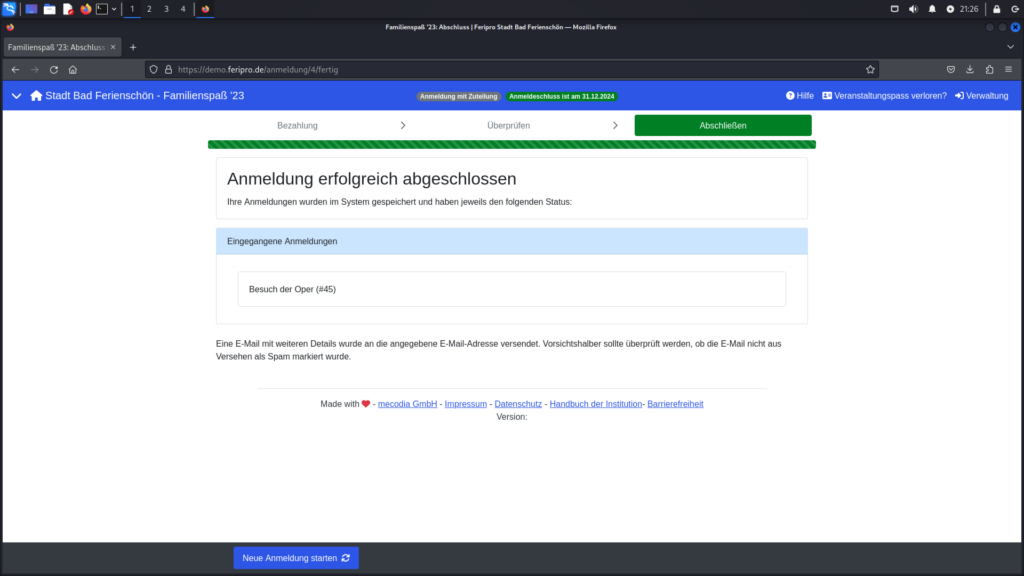
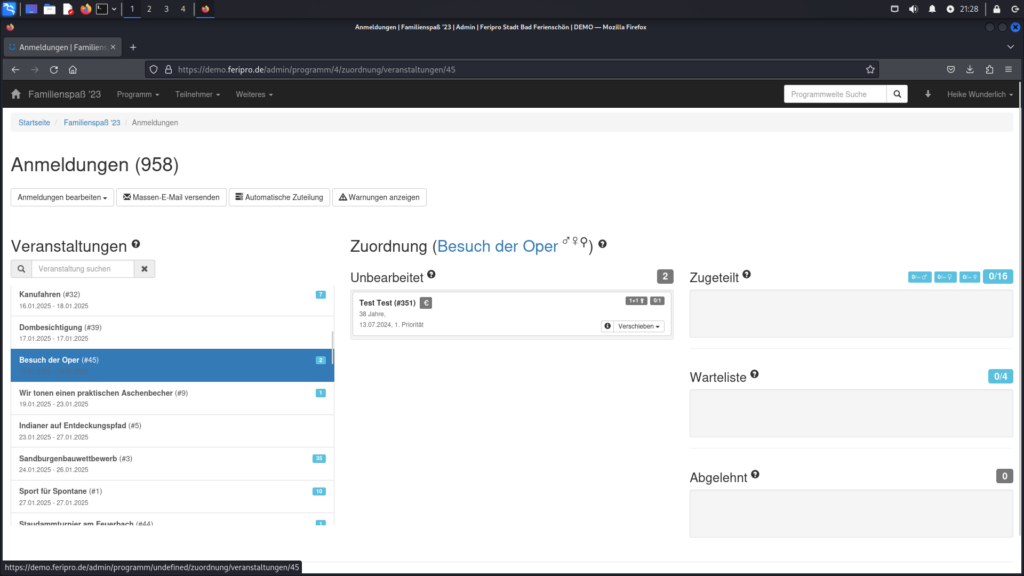
The final two images show the execution of the injected JavaScript code in the registration overview, accessible via the path /admin/programm/<program_id>/zuordnung/veranstaltungen/<event_id>, demonstrating the impact of the stored XSS vulnerability.
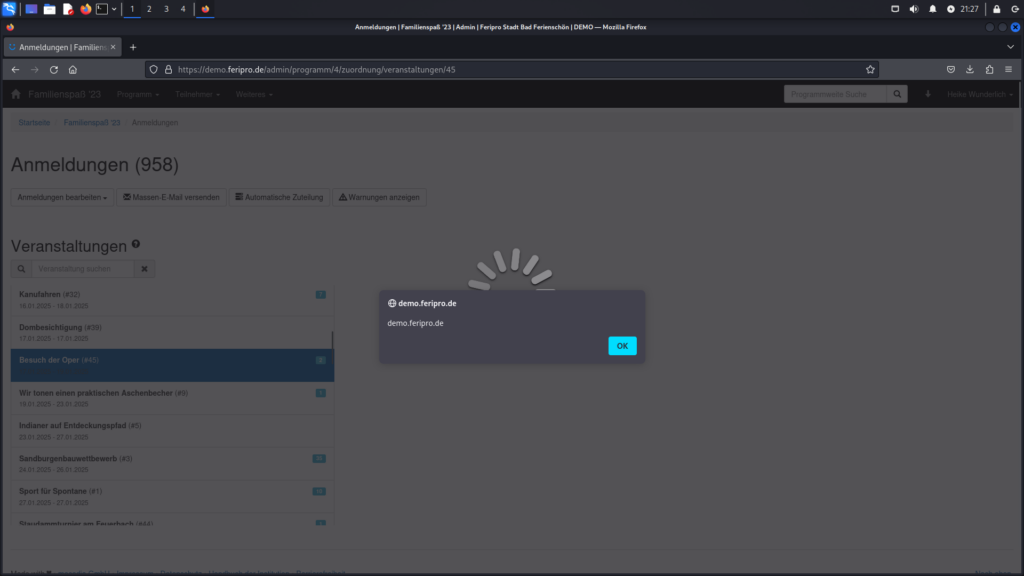
The last image is included to illustrate the interface behavior as a result.
The vulnerabilities were swiftly addressed by the manufacturer, with fixes made available on the same day the issues were reported. Throughout the process, the communication was both friendly and professional, ensuring a smooth and efficient resolution.
Links to further information
- The Feripro software: https://feripro.de/
- The company behind Feripro: https://mecodia.de/
- Incorrect Access Control in the User Management overview (CVE-2024-41517): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41517
- Incorrect Access Control at the Statistics endpoint (CVE-2024-41518): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41518
- Stored Cross-Site Scripting vulnerability in the Event overview (CVE-2024-41519): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41519
History and Updates
The process and how to contact the Feripro team is described below.
07/15/2024 10:14 CEST
Reporting the three vulnerabilities to Feripro. Request the CVEs from the MITRE Corporation and reporting the vulnerabilities to the BSI CERT for information.
07/15/2024 11:15 CEST
Confirmation of the three vulnerabilities by the manufacturer. The manufacturer has been able to reproduce them. A corresponding fix should be available soon.
07/17/2024 05:30 CEST
Feedback from Feripro that the vulnerabilities found have been fixed and have been rolled out to all customer systems since Monday afternoon (07/15/2024).
08/01/2024 10:00 CEST
Public Disclosure of the vulnerability.
References
[2] https://feripro.de/referenzen/


![[DE] Aktueller Stand kryptografischer Verfahren für Web-Applikationen](https://piuswalter.de/wp-content/uploads/aktueller-stand-kryptografischer-verfahren-fur-web-applikationen-400x250.jpg)
0 Kommentare