Who or what is Nitrado?
Nitrado claims to be the worldwide leading service provider in the game server hosting business. It also offers domain and website hosting services.
„Nitrado is the worldwide leading service provider in the sector of game server hosting.“
https://server.nitrado.net/eng/rent-gameserver
In the following post I would like to talk about domain and website hosting services. The positive image of Nitrado in the game server sector is unfortunately not present in the website hosting. Furthermore, it is absolutely insufficient.
But now let’s start from the beginning. I will focus the subject of security in terms of web hosting, email and background architecture.
IT-Security at Nitrado
All of the issues described below have not been resolved as of the publication of this article and were rechecked shortly before publication.
Website hosting
A significant part of all website hosting components is severely outdated. Among them, the version of phpMyAdmin that is vulnerable to known exploits and officially unsupported PHP versions. Also on the production systems running the instances for phpMyAdmin are far from up to date.
PHP versions
Like a large part of all runtime environments, PHP is released in different versions that have a certain lifetime before they are no longer officially supported. The following image shows the release lifecycle of the latest PHP versions.
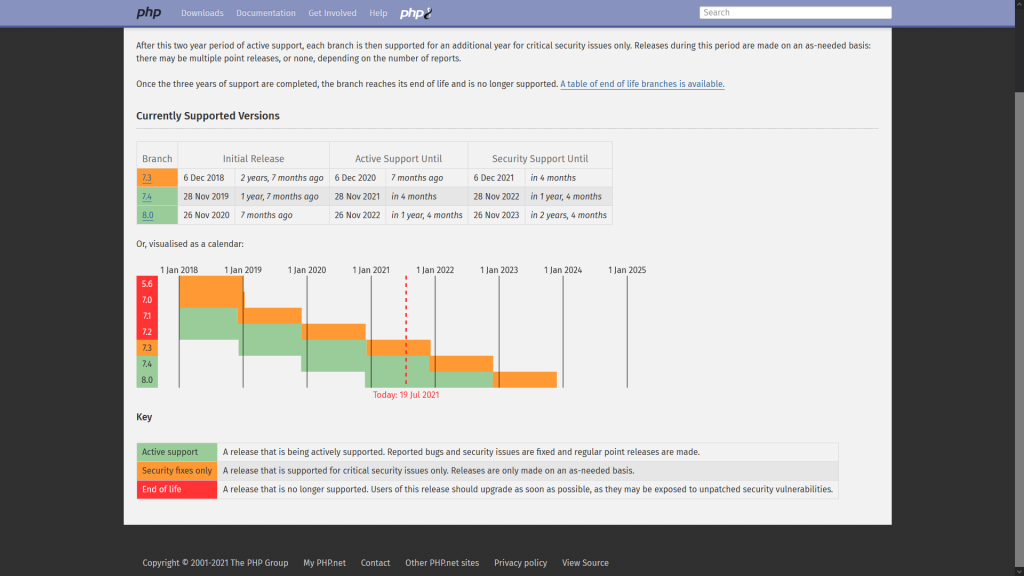
The versions highlighted in red indicate versions that are EOL (end of life), those highlighted in yellow indicate versions for which only critical security patches are created, and those highlighted in green indicate active support. Older versions are listed at Unsupported Branches on the official website of PHP. For example, it can be verified that the PHP 5.3 branch has been expired since 14 Aug 2014, which is 6 years and 11 months ago. But Nitrado offers this version! To make matters worse, there are no versions with active support available as seen in the image below!
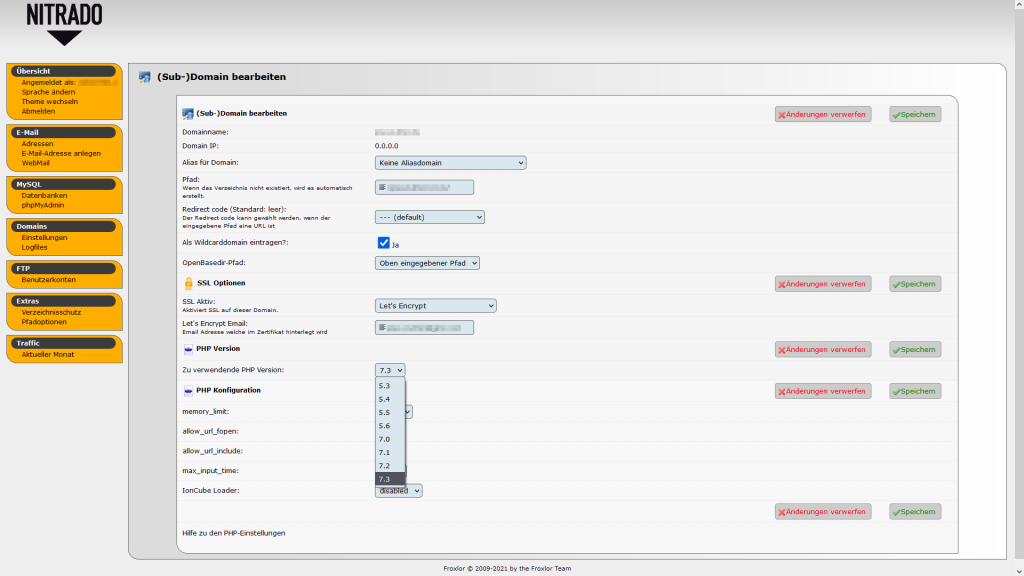
Already on 03/02/2021 a corresponding ticket was opened at Nitrado that pointed out the outdated PHP versions. Except for the repeated answer that no current information is available and patience must be requested, nothing happened.
In the following we will discuss phpMyAdmin hosted by Nitrado, this unfortunately shows even more outdated software and more significant vulnerabilities.
phpMyAdmin version
The developers of phpMyAdmin describe the software as follows.
„phpMyAdmin is a free software tool written in PHP, intended to handle the administration of MySQL over the Web.“
https://www.phpmyadmin.net/
The screenshot shows several fatal problems. These will all be discussed in the following.
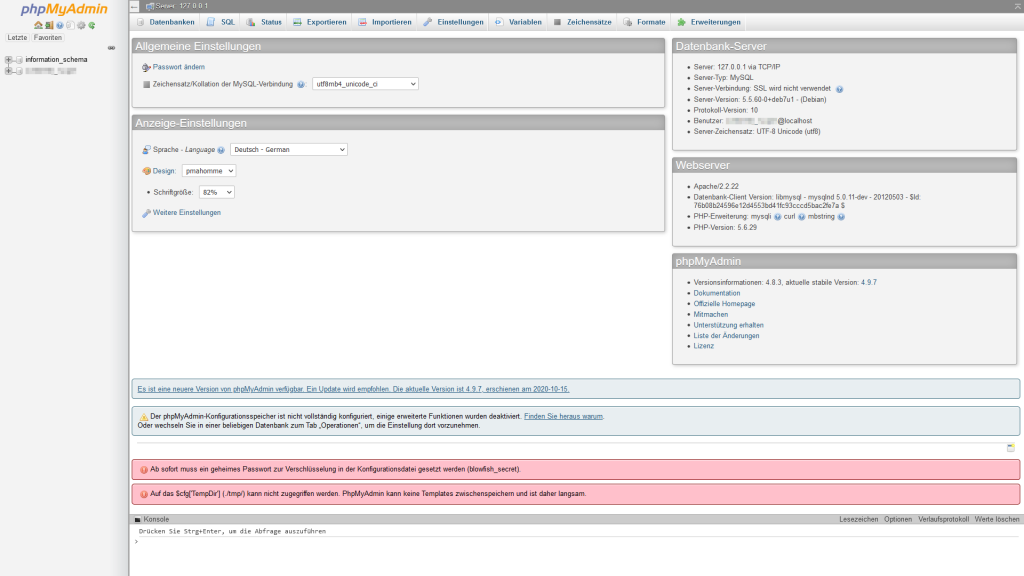
phpMyAdmin notifies with the upper red banner that a secret password for encryption must be set in the configuration file. This is described in the official documentation. The password is used to improve the security of the cookie generation process. However, Nitrado does not have set this password.
It gets more exciting when looking at the environment phpMyAdmin is running on. The following is a comparison of the versions used by Nitrado and the current product versions. The corresponding release dates are given in square brackets below the respective versions.
| Version used by Nitrado [release date] | Latest product version [release date] | |
| MySQL server version | 5.5.60 [19 Apr 2018] | 8.0.25 [11 May 2021] |
| Apache webserver version | 2.2.22 [31 Jan 2012] | 2.4.48 [1 Jun 2021] |
| PHP version | 5.6.29 [8 Dec 2016] | 8.0.8 [1 Jul 2021] |
| phpMyAdmin version | 4.8.3 [22 Aug 2018] | 5.1.1 [4 Jun 2021] |
As you can easily see, a web server released 9 years ago can no longer be secure. Accordingly, there are also many vulnerabilities. If we take a look at www.cvedetails.com, we can already see 13 vulnerabilities for this version. Three of them have a CVSS (Common Vulnerability Scoring System) of 7.5!
Vulnerability CVE-2018-19968
The vulnerability describes the possibility to read local files of the web server by phpMyAdmin. The development team of phpMyAdmin describes the vulnerability on their security website as follows.
„A flaw has been found where an attacker can exploit phpMyAdmin to leak the contents of a local file. The attacker must have access to the phpMyAdmin Configuration Storage tables, although these can easily be created in any database to which the attacker has access. An attacker must have valid credentials to log in to phpMyAdmin; this vulnerability does not allow an attacker to circumvent the login system.“
https://www.phpmyadmin.net/security/PMASA-2018-6/
The MITRE Corporation has also officially assigned a CVE (Common Vulnerabilities and Exposures) to this vulnerability. It can be found as CVE-2018-19968. Based on the phpMyAdmin version found at Nitrado, it is strongly suspected that the exploit can be executed within a few minutes without any further problems.
More vulnerabilities
Apart from this vulnerability, there are several other vulnerabilities listed on the official phpMyAdmin website. These are fixed in newer versions and should thus be installed as soon as possible.
Email security
The security of email sending and receiving is also severely compromised. For example, only outdated protocols are available, which are no longer supported by email clients by default.
The following original answer in german is part of a ticket from 05/12/2021. The English translation is shown in the quote that follows.
„[…] Thunderbird 78 unterstützt in der Standardkonfiguration ausschließlich TLS
1.2. Wenn der Server also noch die deutlich älteren Standards TLS 1.0 oder 1.1
oder gar SSL 3.0 einsetzt, kann der Server nicht mehr direkt mit Thunderbird
genutzt werden. Leider gibt es dazu aber keine individuellen Fehlermeldungen,
daher sind diese Probleme schwer zu erkennen.Unsaubere Kurzzeit-Lösung mit massiven Sicherheitsimplikationen: informiere
Nitrado Support
dich über die Probleme mit der besten vom Server unterstützten TLS-Version.
Wenn Du alle Nachteile dieser Versionen für alle Verbindungen und mit allen
Servern akzeptierst, kannst du in about:config das Feld
’security.tls.version.min‘ auf einen kleineren Wert stellen (iirc ‚1‘ für TLS
1.0, ‚2‘ für TLS 1.1). Schreibe dir deine Änderung irgendwo auf. […]“
The english translation below.
„[…] Thunderbird 78 only supports TLS 1.2 in the default configuration, so if the server is still using the much older standards TLS 1.0 or 1.1 or even SSL 3.0, the server can no longer be used directly with Thunderbird. Unfortunately, however, there are no individual error messages for this, so these problems are difficult to detect.
Unclean short-term solution with massive security implications: find out about the problems with the best TLS version supported by the server. If you accept all disadvantages of these versions for all connections and with all servers, you can change in about:config the field ’security.tls.version.min‘ to a smaller value (iirc ‚1‘ for TLS 1.0, ‚2‘ for TLS 1.1). Write down your change somewhere. […]“
Nitrado Support
Updating background architecture
Due to all these unresolved open vulnerabilities, I personally decided to leave Nitrado in terms of web hosting. I started to set up my own mail server and move it one by one. After the entire configuration was completed and the mail server was working, Nitrado, for its part, changed all DNS entries without permission, without warning, so that the configuration was absolutely useless.
The only answer to a ticket opened for this purpose was that there were corresponding notes in Nitrado’s web interface. Unfortunately, no other notifications were sent in the form of email.
„[…] Leider waren die genannten Umstellungen aus technischer Sicht notwendig, um
weitere Einstellungsmöglichkeiten als auch einen stabileren Service anbieten
zu können.Die Information dass diese Wartungsarbeiten am 7.7.2021 durchgeführt werden,
wurde über eine Woche lang auf unserer Webseite in der Übersicht aller Dienste
entsprechend angezeigt.Dass die Einträge nicht übernommen werden konnten, liegt leider daran, dass
Nitrado Support
das alte und das neue System leider nicht komplett miteinander kompatibel
sind. […]“
The english translation below.
„[…] Unfortunately, the mentioned changes were necessary from a technical point of view in order to be able to offer further setting options as well as a more stable service.
Nitrado Support
The information that this maintenance work will be carried out on 7.7.2021 was displayed accordingly on our website in the overview of all services for over a week.
The fact that the entries could not be transferred is unfortunately due to the fact that the old and the new system are not completely compatible with each other. […]“
All the issues raised here have been reported by me to Nitrado at least once before.
Hopefully, all vulnerabilities will be closed as soon as possible.



0 Kommentare