Abstract
This blog post uncovers several critical vulnerabilities in the CADClick (by KiM GmbH Konstruktion & Internet im Maschinenbau) web application, a widely used digital platform for CAD products. The investigation identified several major security flaws, including:
- A Path Traversal (Local File Inclusion, LFI) vulnerability (CVE-2024-41511).
- A SQL Injection vulnerability (CVE-2024-41512).
- Reflected Cross-Site Scripting vulnerabilities across multiple endpoints (CVE-2024-41513, CVE-2024-41514, CVE-2024-41515, CVE-2024-41516).
These findings highlight the urgent need for rigorous security testing and strong coding practices in web applications, especially those that handle sensitive data and critical functions. This post aims to raise awareness of the importance of proactive security measures in protecting digital assets and maintaining customer trust.
⚠️ Note on Unresolved Vulnerabilities
Unfortunately, not all vulnerabilities have been addressed by the manufacturer by the time of this blog post’s publication. Communication from the manufacturer has been completely absent, resulting in my messages being ignored. After 90 days, as previously announced to the manufacturer and the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI), this blog post has been published. This situation is an exception, as most manufacturers have been open to collaboration, allowing to address and resolve issues together effectively.
What is CADClick?
CADClick i.e. KiM GmbH Konstruktion & Internet im Maschinenbau is a comprehensive digital solution provider offering advanced tools for creating CAD product catalogs, configurators, and BIM technology. They specialize in data creation, UX/UI design, and 3D animation to enhance product visualization and customer experience. Their web application allows businesses to provide CAD products directly to customers, streamlining the design process, improving accuracy, and facilitating better communication between manufacturers and clients.
„CAD/BIM data can be generated worldwide in online or offline libraries and automatically created as 3D PDF data sheets.“
https://www.cadclick.de/en/solutions/cad-product-catalog/
Vulnerabilities in CADClick from KiM
Based on the „Success Stories“ from 67 companies listed on the developer’s website and additional sources, 32 companies have been identified as using this software and being vulnerable. However, it’s crucial to differentiate between the various software versions, as not all are susceptible to common XSS patterns. Additionally, patterns resembling zero-day vulnerabilities have been identified, affecting all versions without any available patch from the manufacturer.
Overview of the Customer-Used Versions of CADClick
The table below outlines the versions of CADClick and the associated libraries used by the identified customers. Following this, the vulnerabilities exploitable at various endpoints will be analyzed. In addition, potential attacks that can be actively executed will also be discussed.
| Company | CADClick ccCatalog | Build | Branch | ccAPI | Statistics database |
|---|---|---|---|---|---|
| https://ace-cad.de/ | DEV 1.11.0 | 20231114.2 | master | 3.4.1.26426 | 1.72.0.0 |
| https://cad.ags-automation.de/ | DEV 1.8.6 – Debug | 20210902.1 | master | 3.3.7.0 | 1.63.0.0 |
| https://cad.alwitra.de/ | DEV 1.11.0 | 20240112.3 | master | 3.4.7.0 | 1.72.0.0 |
| https://cad.baumueller.com/ | DEV 1.11.0 | 20230831.3 | master | 3.3.7.0 | 1.71.0.0 |
| http://cad.br-automation.com/ | DEV 1.11.0 | 20231221.3 | master | 3.4.5.0 | 1.70.0.0 |
| https://cad.pfaff-silberblau.com/ | DEV 1.8.6 – Debug | 20210916.1 | master | 3.3.6.0 | 1.60.0.0 |
| https://cad.dunkermotoren.de/ | DEV 1.8.3 – Debug | 20190429.2 | 1.8.3 | 3.2.5.0 | 1.50.0.0 |
| https://konfig.ernstschweizer.ch/ | DEV 1.8.3 – Debug | 19700101.1 | 3.2.5.0 | 1.45.0.0 | |
| https://cad.fischer.de/ | DEV 1.11.0 | 20231115.2 | master | 3.4.7.0 | 1.70.0.0 |
| https://cad.georgfischer.com/ | DEV 1.11.0 | 20240123.1 | master | 3.2.5.0 | 1.70.0.0 |
| https://teccad.hafele.com/ | DEV 1.9.0 – Debug | 20220908.3 | master | 3.4.4.28525 | 1.67.0.0 |
| https://cadbox.heidenhain.de/ | REL 1.7.2.5 – Debug | 20180522145050 | 3.1.5.0 | n/a | |
| https://cad.herborner-pumpen.de/kim/ | DEV 1.10.0 | 20230428.3 | master | 3.3.2.0 | 1.70.0.0 |
| https://cad.hiwin.de/ | DEV 1.11.0 | 20231130.2 | master | 3.3.7.0 | 1.72.0.0 |
| https://www.igus-cad.com/ | DEV 1.11.0 | 20240410.1 | master | 3.4.7.0 | 1.71.0.0 |
| https://bimconfig.lamilux.de/ | DEV 1.10.0 | 20230420.1 | master | 3.3.7.0 | 1.70.0.0 |
| https://cad.meusburger.com/ | DEV 1.11.0 | 20230901.1 | master | 3.4.3.0 | 1.70.0.0 |
| https://cad.minitec.de/ | DEV 1.10.0 | 20230419.2 | master | 3.4.4.0 | 1.72.0.0 |
| https://cad.murtfeldt.de/ | DEV 1.11.0 | 20240119.2 | master | 3.4.7.0 | 1.72.0.0 |
| https://peraqua.cadclick.com/ | DEV 1.10.0 | 20230421.2 | master | 3.3.7.0 | 1.70.0.0 |
| https://cad.poeppelmann.com/ | DEV 1.10.0 | 20230421.2 | master | 3.3.7.0 | 1.72.0.0 |
| https://cad.reca.com/ | DEV 1.8.6 – Debug | 20220427.2 | master | 3.3.7.0 | 1.66.0.0 |
| https://cad.sbn.de/ | DEV 1.6 – Debug | 20170726101702 | 3.1.5.0 | ||
| https://cad.schoeck.de/ | DEV 1.11.0 | 20240318.1 | master | 3.4.5.0 | 1.72.0.0 |
| https://cad.sitema.de/ | DEV 1.8.6 – Debug | 20210708.1 | master | 3.3.7.0 | 1.64.0.0 |
| http://stabilus.cadclick.com/ | DEV 1.11.0 | 20230615.3 | master | 3.3.7.0 | 1.70.0.0 |
| https://cad.phoenixcontact.com/ | DEV 1.8.6 – Debug | 20210413.2 | master | 3.4.4.0 | none |
| https://cad.tecnorm.de/ | DEV 1.11.0 | 20231019.1 | master | 3.4.5.0 | 1.70.0.0 |
| https://konfigurator.tjiko.de/ | DEV 1.11.0 | 20231117.2 | master | 3.4.6.0 | 1.70.0.0 |
| https://cad.wuerth.com/ | DEV 1.11.0 | 20240613.2 | master | 3.4.7.0 | 1.72.0.0 |
| https://cad.vogel-antriebe.de/ | 1.0.4577.42 – Debug | 2.8.19.69 | |||
| https://cad.fittings.at/ | 1.0.4801.6 – Debug | 2.8.19.69 |
Reflected XSS on Various Endpoints (CVE-2024-41513, CVE-2024-41514, CVE-2024-4151, CVE-2024-41516)
CADClick is developed in C# using the ASP.NET web application framework. The following endpoints have been identified as vulnerable to Reflected XSS attacks:
Artikel.aspx(parametersearchindex) (CVE-2024-41513)PrevPgGroup.aspx(parameterwer) (CVE-2024-41514)ccHandlerResource.ashx(parameterres_url) (CVE-2024-41515)ccHandler.aspx(parameterbomid) (CVE-2024-41516)
The image below demonstrates the reflected XSS vulnerability on the Artikel.aspx endpoint. The payload <script>alert(location.hostname)</script> can be used to exploit this flaw. It’s important to note that this vulnerability is not present in all versions of CADClick.
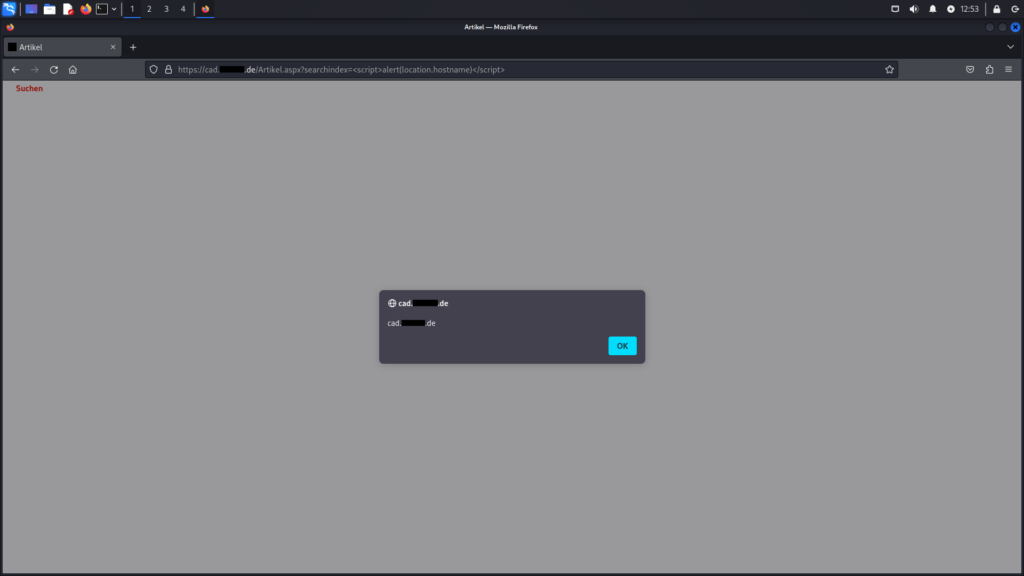
Artikel.aspx endpointThe same vulnerability applies to the PrevPgGroup.aspx endpoint. The same payload, <script>alert(location.hostname)</script>, can be used here as well. However, like the previous example, this endpoint is only vulnerable in specific versions of CADClick.
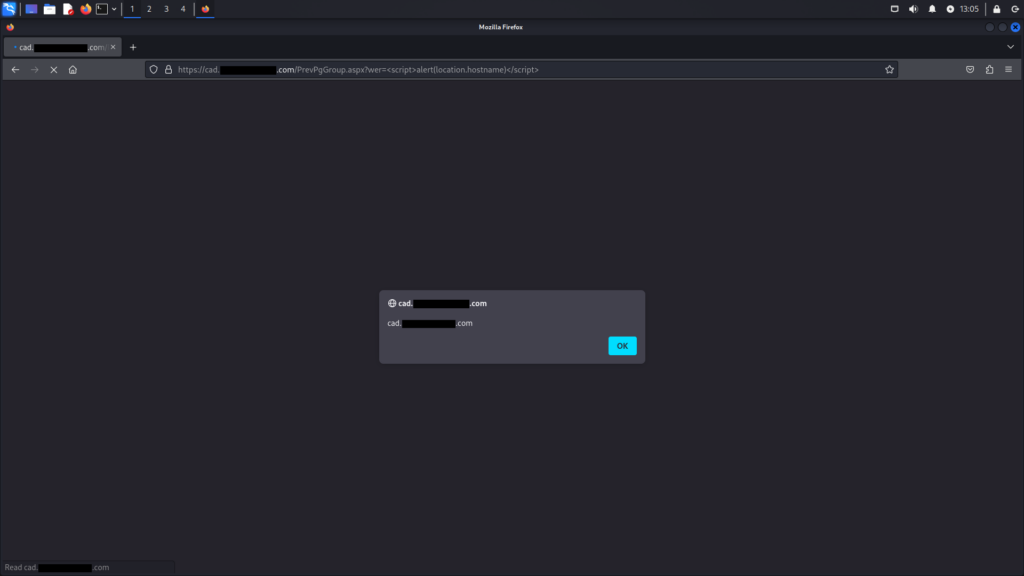
PrevPgGroup.aspx endpointThe image below displays a version of CADClick that is not susceptible to the vulnerability. In this version, special characters such as <, >, (, ), ;, ', and " are automatically replaced with underscores (_), preventing the XSS exploit.
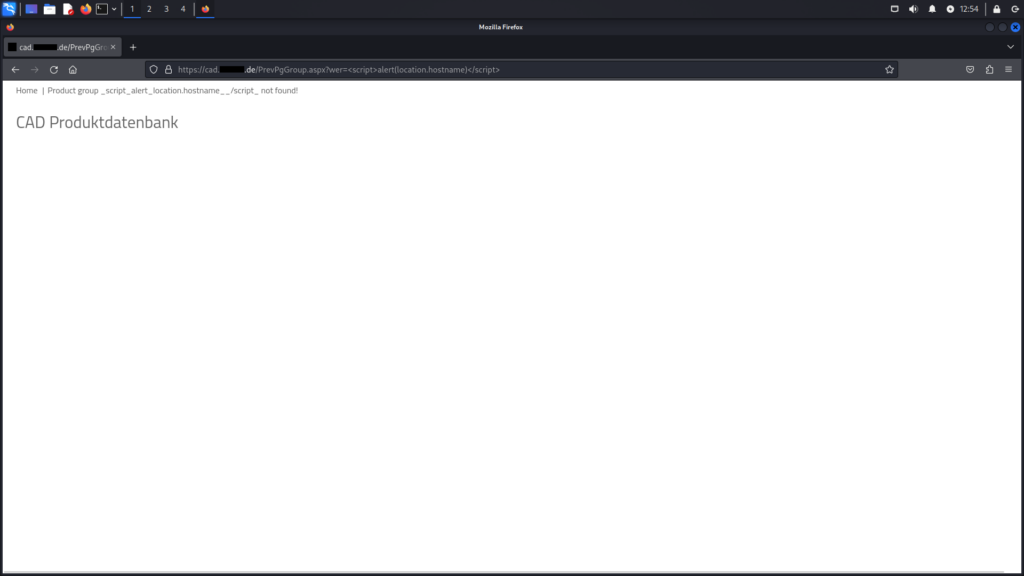
PrevPgGroup.aspx endpointThe ccHandlerResource.ashx endpoint, specifically with the parameter res_url is also vulnerable to Reflected XSS attacks.
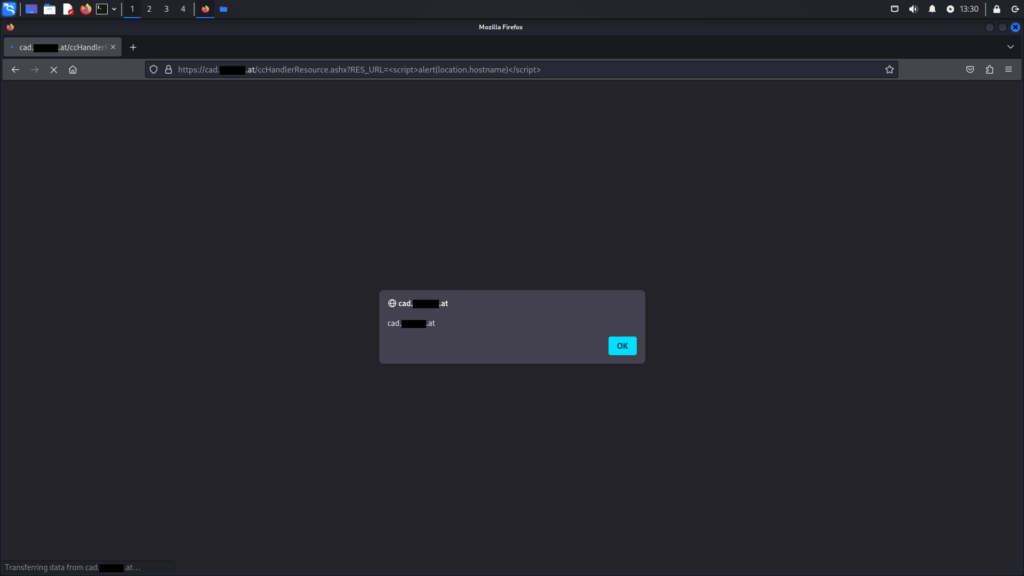
ccHandlerResource.ashxThe ccHandler.aspx endpoint is vulnerable to multiple security issues, including Reflected XSS and SQL Injection attacks. When accessed without parameters, it reveals available and vulnerable parameters, providing insight into potential exploitation points.
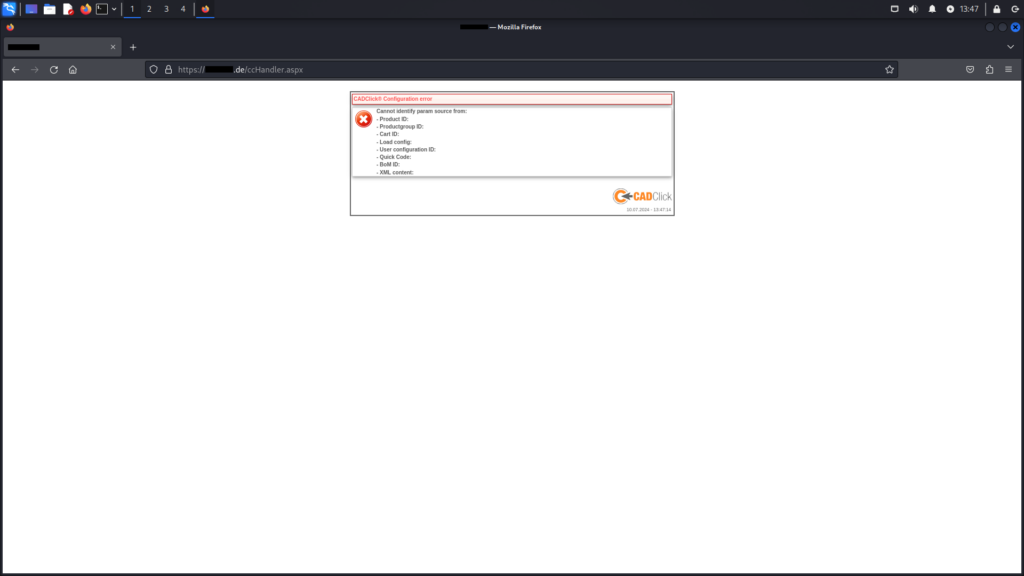
ccHandler.aspx endpoint without parametersTesting with the BoM ID using the guessed parameter bomid and a slightly adjusted payload proves successful. This demonstrates the endpoint’s vulnerability to the Reflected XSS attack.
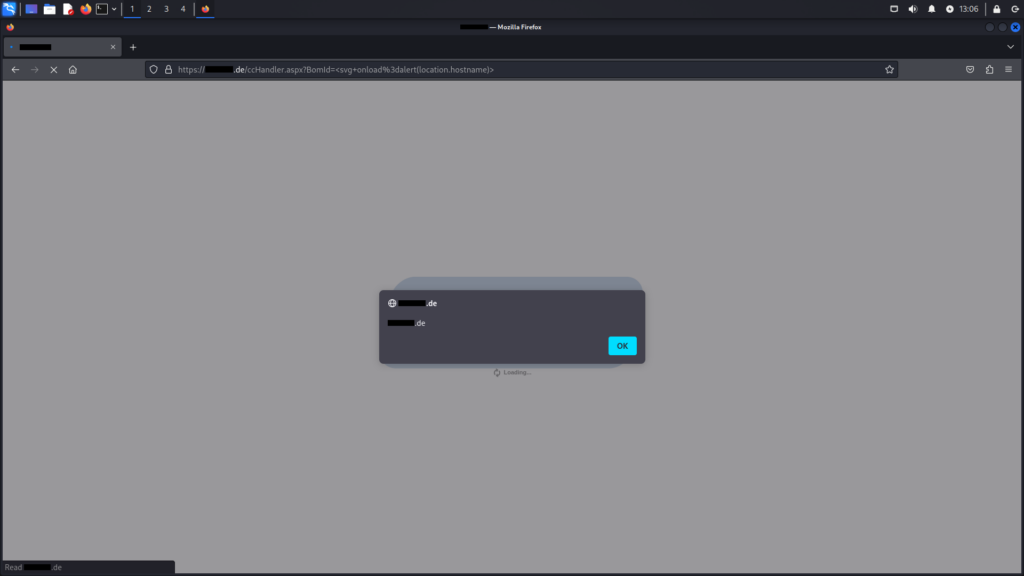
ccHandler.aspx endpointAfter confirming the pop-up window, an intriguing error message appeared. The space in the error message revealed the SVG, which was inserted with the payload. More notably, the error indicated a SQL syntax issue near the character '. This raises the possibility of an additional vulnerability in the application.
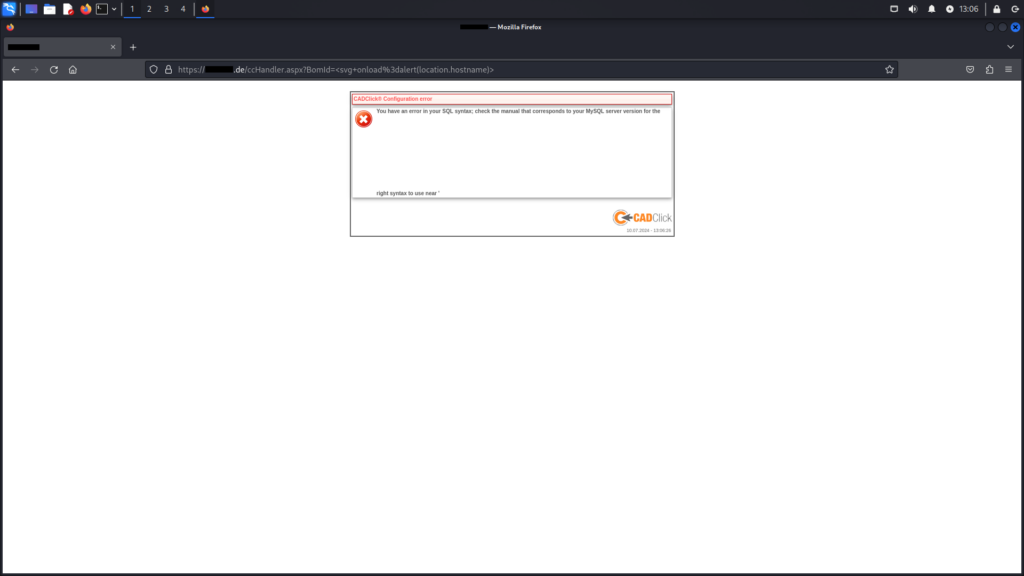
ccHandler.aspx endpointSQL Injection Possibilities (CVE-2024-41512)
SQL Injection attacks are also effective. As noted earlier, this vulnerability impacts numerous customers. During an assessment of other clients, a case was found with extensive logging enabled. This logging not only displays the SQL query but also specifies the exact location of the error on the server, providing insights into the directory structure used. A closer examination reveals important details.
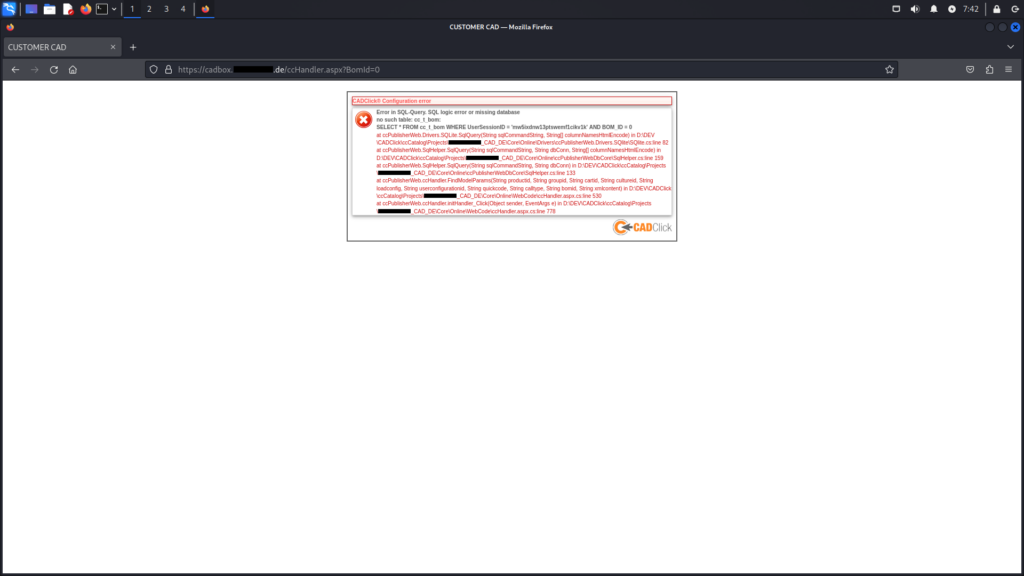
ccHandler.aspx endpointBy appending the payload and 1=2 union all select concat_ws(0x3a,version(),user(),database()) to the previous URL, an error message was generated. This indicates that the SQL query was successfully appended to the original query.
Unfortunately, explicit output of information regarding the endpoints was not achievable at this time. It would be advisable for the manufacturer to conduct further investigation into this matter.
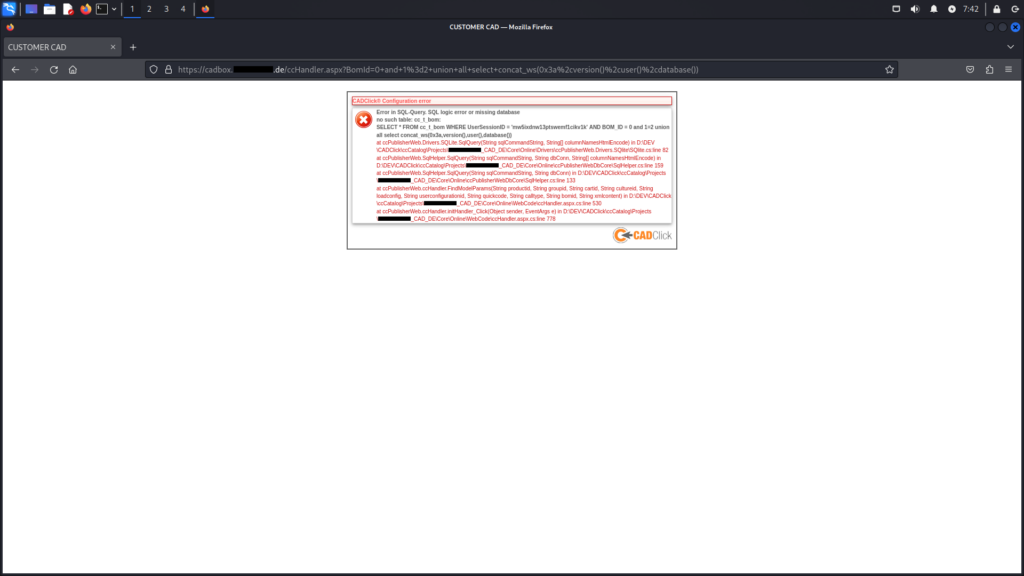
ccHandler.aspx endpointPath Traversal (Local File Inclusion) Vulnerability (CVE-2024-41511)
Subsequent examination of the web application aimed to identify additional endpoints where vulnerabilities might exist. This leads to the discovery of a Local File Inclusion (LFI) vulnerability, which can be exploited through the BinaryFileRedirector.ashx endpoint using the path parameter.
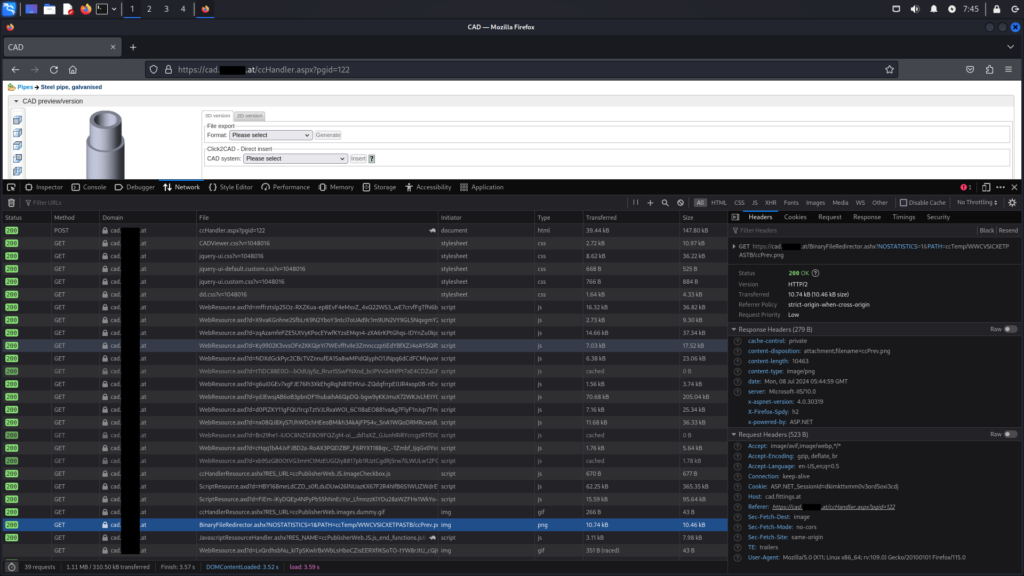
When the request shown in the above screenshot is made, the specified image provided as a parameter is returned and subsequently downloaded by the web browser.
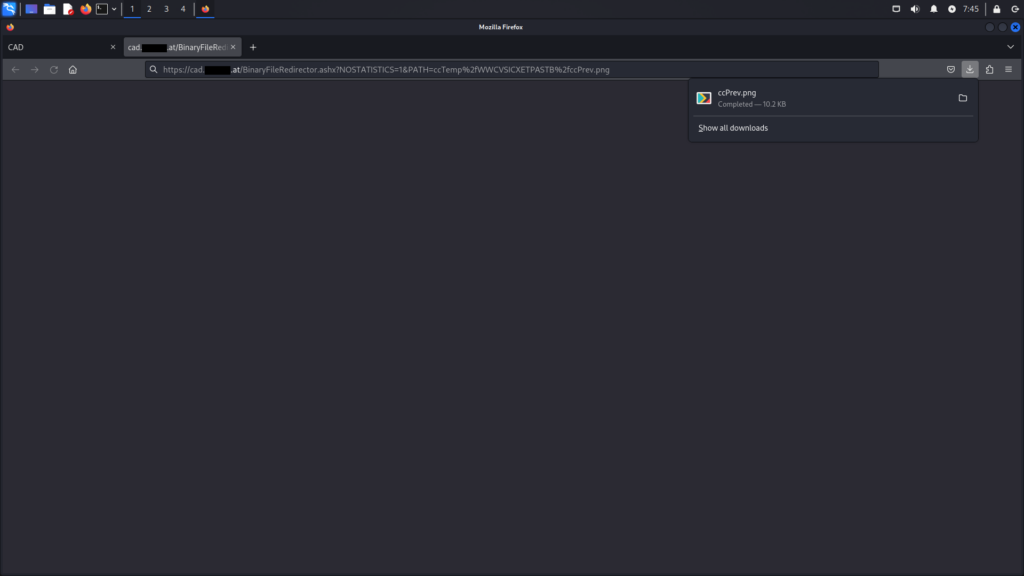
BinaryFileRedirector.ashx endpointThe next logical step involves attempting to access system files through the endpoint. This is illustrated below using the paths C:\Windows\win.ini and C:\Windows\system.ini. As demonstrated, this method allows for the reading of system files.
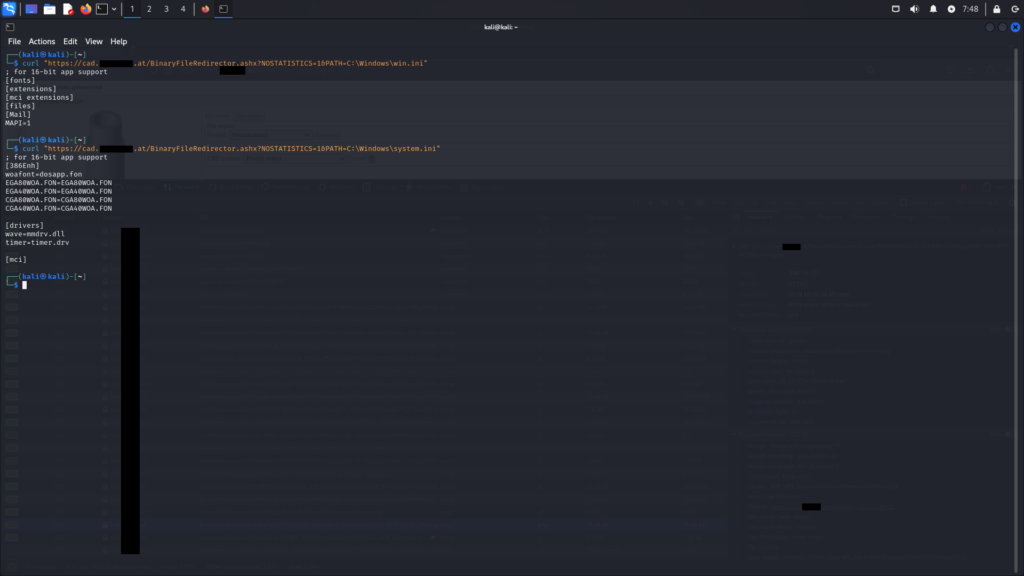
BinaryFileredirector.ashx endpointAt this point, it is concluded that further testing of the web application is unwarranted, at least until the manufacturer addresses and rectifies the known vulnerabilities across all endpoints. However, numerous indications suggest that the application harbors many other vulnerabilities, potentially including artificial ones, which could be exploited to compromise the underlying system for at least 32 customers.
What’s the Outcome?
The findings from this investigation underscore significant security risks associated with the CADClick web application, including multiple critical vulnerabilities. Despite attempts to engage with the manufacturer, no communication has been received, leaving some of these issues unresolved. The lack of response highlights a concerning trend in vulnerability management, emphasizing the necessity for proactive security measures in software development. It is imperative for developers to prioritize the identification and remediation of vulnerabilities to protect sensitive data and maintain user trust.
Additional Resources and References
- The company behind CADClick: https://www.cadclick.de/
- Coordinated Vulnerability Disclosure (CVD) process of the BSI: https://www.bsi.bund.de/dok/schwachstellenmeldung
- Path Traversal (Local File Inclusion, LFI) vulnerability (CVE-2024-41511): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41511
- SQL Injection vulnerability (CVE-2024-41512): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41512
- Reflected Cross-Site Scripting vulnerability in the
Artikel.aspxendpoint (CVE-2024-41513): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41513 - Reflected Cross-Site Scripting vulnerability in the
PrevPgGroup.aspxendpoint (CVE-2024-41514): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41514 - Reflected Cross-Site Scripting vulnerability in the
ccHandlerResource.ashxendpoint (CVE-2024-41515): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41515 - Reflected Cross-Site Scripting vulnerability in the
ccHandler.aspxendpoint (CVE-2024-41516): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-41516
History and Updates
The process and how to contact the CADClick team is described below.
07/05/2024 11:48 CEST
At the beginning, I identified only the XSS vulnerability and promptly notified the CADClick team via email.
07/08/2024 11:12 CEST
Over the weekend, I discovered additional vulnerabilities, including more XSS and LFI issues, as well as opportunities for SQL injections. On Monday, I highlighted the critical nature of these findings in another email.
07/11/2024 11:11 CEST
After not receiving a response to my email from CADClick, I took the initiative to find the managing director’s email address and wrote to him directly.
07/12/2024 12:34 CEST
After receiving no response from the manufacturer, I reported the vulnerabilities to the BSI CERT to facilitate communication with the manufacturer and coordinate the CVD process.
08/06/2024 10:15 CEST
There has still been no feedback from the manufacturer; however, numerous changes have been implemented in customer systems concerning IT security. The versioning remains inconsistent.
Further communication with the BSI CERT confirmed that no feedback has been received from the manufacturer on their end either. The BSI has followed up again and requested an evaluation by 08/14/2024.
08/13/2024 13:51 CEST
Feedback from BSI CERT indicated that the manufacturer has acknowledged the vulnerabilities and is actively working on their remediation. Processing is expected to be completed in the coming days, with updates to be communicated to customers as necessary. Additionally, the BSI has suggested that specific information be sent to me.
09/27/2024 12:21 CEST
I emailed BSI CERT, indicating that the vulnerabilities will be published on 10/04/2024, as previously communicated to the manufacturer on 07/08/2024. There has been no communication from the manufacturer since then.
10/04/2024 00:00 CEST
Public Disclosure of the vulnerabilities.
Yet there has still been no response from the manufacturer regarding the matter. Some of the vulnerabilities are still present in the customer systems.


![[DE] Aktueller Stand kryptografischer Verfahren für Web-Applikationen](https://piuswalter.de/wp-content/uploads/aktueller-stand-kryptografischer-verfahren-fur-web-applikationen-400x250.jpg)
0 Kommentare